Tuesday, April 24, 2012
BoepClub
So we have a proper club now called BoepClub, it is made up of the following members: (at one stage you had to have someone with the same name if you wanted in)
- Andrew H
- Andrew M
- Craig B
- Craig E
- Shaun K
- Sean Rose
- Chris K
- Chris S
- Jacques H
- Adrian DH
- Mike M
- ?
Thursday, September 16, 2010
N+ Damelin
So, we still dont have our results for the course! Seriously taking a long time - I guess it is what to be expected after the course was run so badly! Damelin really dropped the ball in the instance!!!
Well I was able to get the results of my exam "unofficially" I didn't make it to top of the class but 2nd will have to do at 97%. Whoohoo!
I guess that the Blog can go back to toys now!
Well I was able to get the results of my exam "unofficially" I didn't make it to top of the class but 2nd will have to do at 97%. Whoohoo!
I guess that the Blog can go back to toys now!
Friday, March 26, 2010
Lesson 12 and 13
Lesson 12
TCP/IP Protocol Suite
The internet Protocol – (IP)
This serves to assign the correct destination address to a data packet. IP uses subnet mask to determine the if the receiving node is on the same subnet or a remote network and delivers the packet.
The address Resolution Protocol (ARP)
Address resolution protocol supports the internet protocol by resolving IP addresses to the MASC address.
Reverse Address Resolution Protocol (RARP)
RARP is a protocol that allows a node on a local area network to discover its IP address from a routers ARP table or cache.
The Internet Control Message Protocol (ICMP)
The internet control message protocol is a service added to the IP protocol that attempts to report on the condition of the connection, ICMP messages notify a sender of network conditions by reporting IP errors.
The Internet Management Protocol (IGMP)
IGMP supports multicasting in a routed environment. The router uses the IMGP to poll its interfaces for members of the multicast group and the forwards the multicast transmission to the group members.
PORTS
All ports are assigned a number in a range from 0 – 65535. The IANA separates the port numbers into three blocks:
1. Well known ports, which are assigned by system process by IANA
2. Registered ports, which are available to user processes and are listed as a convenience by IANA
3. Dynamic ports, this are assigned by a client operating system as needed when there is a request for service.
Port Ranges, well know/used ports:
• 21 – ftp (file transfer protocol) used for download
• 23 – Telnet, remote login protocol
• 25 – SMTP (simple mail transfer protocol) used for sending mail
• 53 – dns (domain name service) changes the IP address into a user-friendly name
• 80 – http (hypertext transfer protocol) internet access
• 110 – pop3 (post office protocol number 3)
• 143 – impa (internet message access protocol)
• 161 – snmp (simple network management protocol)
• 443 – https (secure http)
UDP ports:
• 7 – echo (PING)
• 123 – ntp (network time protocol)
Sockets
A socket is a piece of software within an operating system that connects an application with a network protocol.
IP Address Assignment Methods
Static and Dynamic addressing – IP addresses can either be assigned manually to make them static to a node on the network or it can be assigned dynamically by the DHCP service.
DHCP – Dynamic Host Configuration Protocol
DHCP is a network service that provides automatic assignment of IP addresses and other TCP/IP configuration information in the network nodes that are configured as DHCP clients.
DHCP Lease process
APIPA – Automatic Private IP Addressing
APIPA is a service that enables a DHCP client computer to configure itself automatically with an IP Address in the range of 169.254.0.1 to 169.254.255.254 if no DHCP servers respond to the clients DHCP discover broadcast.
The Ping utility:
You can ping a computer to confirm its connectivity to a network.
Ping options are as follows:
You can ping by IP address
You can ping the loopback address (127.0.0.1) to test whether TCP/IP has initialised on an individual system. If the computer has a default gateway, you can ping the remote system.
Some of the options include setting up the packet size, changing the time to live (TTL) value and specify how many times to ping the host.
Ping Blocking
As a security measure, some public internet hosts and internet routers might be configured to block incoming packets that are generated by that ping command.
IP Configuration Utilities.
Winipcfg – Windows 98, 95, ME
Ipconfig – Server 2008, 2003 and windows 2000 as well as XP Vista and NT
Ifconfig – Linux and UNIX
Dhclient – Linux and UNIX (the dhclient utility allows you to configure and manage dhcp settings the network interfaces on a computer.
Ipconfig Commands for DHCP: (for enabling dynamic address lease management)
Ipconfig/release – forces the release of the IP address of a network connection
Ipconfig/renew – request the renewal of the lease.
If the DHCP is non-responsive, the server will revert to the APIPA.
DNS – Domain Name System
The DNS is a TCP/IP name resolution service that translates FQDN’s into IP addresses. It consists of a system of databases that are stored on separate DNS servers on all networks that are connected to the Internet. All servers work together to resolve the FQDN’s (Fully Qualified Doman Name). On internal networks a local DNS service can resolve host names without using the external DNS servers.
The HOSTS file
A HOSTS file is a plain text file configured on a client machine containing a list of IP addresses and their associated host names.
The HOSTS file provides an alternative method of host name resolution. An external client can use a HOSTS file to resolve names on your internal network without needing to access to your internal DNS server.
NetBIOS Names
NEtBIOS names are computer names that take a 16-byte common name format developed by IBM and Microsoft to identify the network devices. Fifteen bytes represent characters in the name; the hidden 16th byte is a code to denote the type of service provided by the device. NetBIOS names must be unique on the network.
NetBIOS Name Resolution Methods:
• NetBIOS broadcast name resolution – for data delivery, NetBIOS names must be resolved to the MAC addresses.
• WINS – WINS is Microsoft’s NetBIOS name server which was developed to reduce the number of NetBIOS name resolution broadcasts.
• The LMHOSTS File – an LMHOSTS file is a text file that contains NetBIOS name-to-IP Address mappings, each on a separate line. The IP address is listed first, then a space, and then the associated NetBIOS name.
TCP/IP Protocol Suite
The internet Protocol – (IP)
This serves to assign the correct destination address to a data packet. IP uses subnet mask to determine the if the receiving node is on the same subnet or a remote network and delivers the packet.
The address Resolution Protocol (ARP)
Address resolution protocol supports the internet protocol by resolving IP addresses to the MASC address.
Reverse Address Resolution Protocol (RARP)
RARP is a protocol that allows a node on a local area network to discover its IP address from a routers ARP table or cache.
The Internet Control Message Protocol (ICMP)
The internet control message protocol is a service added to the IP protocol that attempts to report on the condition of the connection, ICMP messages notify a sender of network conditions by reporting IP errors.
The Internet Management Protocol (IGMP)
IGMP supports multicasting in a routed environment. The router uses the IMGP to poll its interfaces for members of the multicast group and the forwards the multicast transmission to the group members.
PORTS
All ports are assigned a number in a range from 0 – 65535. The IANA separates the port numbers into three blocks:
1. Well known ports, which are assigned by system process by IANA
2. Registered ports, which are available to user processes and are listed as a convenience by IANA
3. Dynamic ports, this are assigned by a client operating system as needed when there is a request for service.
Port Ranges, well know/used ports:
• 21 – ftp (file transfer protocol) used for download
• 23 – Telnet, remote login protocol
• 25 – SMTP (simple mail transfer protocol) used for sending mail
• 53 – dns (domain name service) changes the IP address into a user-friendly name
• 80 – http (hypertext transfer protocol) internet access
• 110 – pop3 (post office protocol number 3)
• 143 – impa (internet message access protocol)
• 161 – snmp (simple network management protocol)
• 443 – https (secure http)
UDP ports:
• 7 – echo (PING)
• 123 – ntp (network time protocol)
Sockets
A socket is a piece of software within an operating system that connects an application with a network protocol.
IP Address Assignment Methods
Static and Dynamic addressing – IP addresses can either be assigned manually to make them static to a node on the network or it can be assigned dynamically by the DHCP service.
DHCP – Dynamic Host Configuration Protocol
DHCP is a network service that provides automatic assignment of IP addresses and other TCP/IP configuration information in the network nodes that are configured as DHCP clients.
DHCP Lease process
APIPA – Automatic Private IP Addressing
APIPA is a service that enables a DHCP client computer to configure itself automatically with an IP Address in the range of 169.254.0.1 to 169.254.255.254 if no DHCP servers respond to the clients DHCP discover broadcast.
The Ping utility:
You can ping a computer to confirm its connectivity to a network.
Ping options are as follows:
You can ping by IP address
You can ping the loopback address (127.0.0.1) to test whether TCP/IP has initialised on an individual system. If the computer has a default gateway, you can ping the remote system.
Some of the options include setting up the packet size, changing the time to live (TTL) value and specify how many times to ping the host.
Ping Blocking
As a security measure, some public internet hosts and internet routers might be configured to block incoming packets that are generated by that ping command.
IP Configuration Utilities.
Winipcfg – Windows 98, 95, ME
Ipconfig – Server 2008, 2003 and windows 2000 as well as XP Vista and NT
Ifconfig – Linux and UNIX
Dhclient – Linux and UNIX (the dhclient utility allows you to configure and manage dhcp settings the network interfaces on a computer.
Ipconfig Commands for DHCP: (for enabling dynamic address lease management)
Ipconfig/release – forces the release of the IP address of a network connection
Ipconfig/renew – request the renewal of the lease.
If the DHCP is non-responsive, the server will revert to the APIPA.
DNS – Domain Name System
The DNS is a TCP/IP name resolution service that translates FQDN’s into IP addresses. It consists of a system of databases that are stored on separate DNS servers on all networks that are connected to the Internet. All servers work together to resolve the FQDN’s (Fully Qualified Doman Name). On internal networks a local DNS service can resolve host names without using the external DNS servers.
The HOSTS file
A HOSTS file is a plain text file configured on a client machine containing a list of IP addresses and their associated host names.
The HOSTS file provides an alternative method of host name resolution. An external client can use a HOSTS file to resolve names on your internal network without needing to access to your internal DNS server.
NetBIOS Names
NEtBIOS names are computer names that take a 16-byte common name format developed by IBM and Microsoft to identify the network devices. Fifteen bytes represent characters in the name; the hidden 16th byte is a code to denote the type of service provided by the device. NetBIOS names must be unique on the network.
NetBIOS Name Resolution Methods:
• NetBIOS broadcast name resolution – for data delivery, NetBIOS names must be resolved to the MAC addresses.
• WINS – WINS is Microsoft’s NetBIOS name server which was developed to reduce the number of NetBIOS name resolution broadcasts.
• The LMHOSTS File – an LMHOSTS file is a text file that contains NetBIOS name-to-IP Address mappings, each on a separate line. The IP address is listed first, then a space, and then the associated NetBIOS name.
Friday, March 5, 2010
Lesson 11
Quick Recap of Lesson 10:
Key Acronym: OSPF – open shortest path first!
Classfull and Classless IP Addresses:
A 1 – 127 255.0.0.0
B 128 – 191 255.255.0.0
C 192 – 223 255.255.255.0
127 is used for pinging thus is completely excluded. There are also classes D and E but we do not need to know them just that they are there.
The default Subnet mask looks like: 255(which is network).0.0.0 (which are the nodes)
Subnet masking is for:
1. Manipulating collision domains
2. Calculating how many nodes are available on a network
Network ID
If the network ID is 121.0.0.1 then the first usable address would be 121.0.0.2
Custom IP Addresses
TCP/IP Subnets
• TCP/IP is a subnet class of leased addresses that has been divided up into smaller groups to serve all the network needs. A custom TCP/IP subnet has a custom subnet mask and ANDed to the IP Address, so that what the node sees as its local network is a subset of the whole default network address block.
• A default gateway is configured for each subnet to route traffic between the subnets.
Custom subnet masks:
• Custom Subnet masks on a Class C Network
Last octet of New Mask in Binary – New Mask Decimal - # of added networks – Nodes per network
10000000 255.255.255.128 2 126
11000000 255.255.255.192 4 62
11100000 255.255.255.224 8 30
11110000 255.255.255.240 16 14
11111000 255.255.255.248 32 6
11111100 255.255.255.252 64 2
To determine available host addresses:
The number of host address on a custom subnet is a function of the total number of address bits available for host addressing. The formula is 2 to the power or x – 2 where x is the number of host bits!
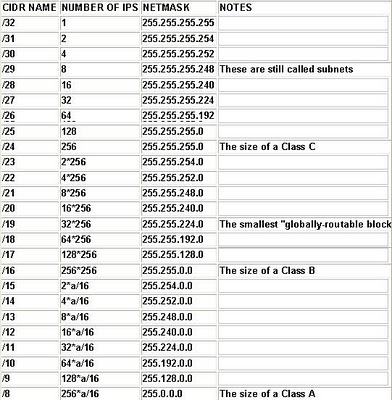
Classless Inter Domain Routing (CIDR)
• CIDR is a subnetting method that treats a VLSM as a 32 bit binary word. The mask bits can move in one bit increments to provide the exact number of nodes and networks required. CIDR notation combimes the network address with a single number to represent the number of one bits in the mask. With CIDR, multiple class based networks can be represented as a single block.
The TCP/IP Protocol Suite:
The TCP/IP Network model is a 4 layer network model which loosely follows the OSI model, the application layer maps the application, presentation and session layers in the OSI model.
3 things to remember to configure on a PC for TCP/IP addressing:
1. IP Address\
2. Subnet Mask
3. Default Gateway
Classless IP’s
How to determine your network ID?
How to determine your network mask?
EASY – RUN, CMD, ipconfig all
Key Acronym: OSPF – open shortest path first!
Classfull and Classless IP Addresses:
A 1 – 127 255.0.0.0
B 128 – 191 255.255.0.0
C 192 – 223 255.255.255.0
127 is used for pinging thus is completely excluded. There are also classes D and E but we do not need to know them just that they are there.
The default Subnet mask looks like: 255(which is network).0.0.0 (which are the nodes)
Subnet masking is for:
1. Manipulating collision domains
2. Calculating how many nodes are available on a network
Network ID
If the network ID is 121.0.0.1 then the first usable address would be 121.0.0.2
Custom IP Addresses
TCP/IP Subnets
• TCP/IP is a subnet class of leased addresses that has been divided up into smaller groups to serve all the network needs. A custom TCP/IP subnet has a custom subnet mask and ANDed to the IP Address, so that what the node sees as its local network is a subset of the whole default network address block.
• A default gateway is configured for each subnet to route traffic between the subnets.
Custom subnet masks:
• Custom Subnet masks on a Class C Network
Last octet of New Mask in Binary – New Mask Decimal - # of added networks – Nodes per network
10000000 255.255.255.128 2 126
11000000 255.255.255.192 4 62
11100000 255.255.255.224 8 30
11110000 255.255.255.240 16 14
11111000 255.255.255.248 32 6
11111100 255.255.255.252 64 2
To determine available host addresses:
The number of host address on a custom subnet is a function of the total number of address bits available for host addressing. The formula is 2 to the power or x – 2 where x is the number of host bits!
Classless Inter Domain Routing (CIDR)
• CIDR is a subnetting method that treats a VLSM as a 32 bit binary word. The mask bits can move in one bit increments to provide the exact number of nodes and networks required. CIDR notation combimes the network address with a single number to represent the number of one bits in the mask. With CIDR, multiple class based networks can be represented as a single block.
The TCP/IP Protocol Suite:
The TCP/IP Network model is a 4 layer network model which loosely follows the OSI model, the application layer maps the application, presentation and session layers in the OSI model.
3 things to remember to configure on a PC for TCP/IP addressing:
1. IP Address\
2. Subnet Mask
3. Default Gateway
Classless IP’s
How to determine your network ID?
How to determine your network mask?
EASY – RUN, CMD, ipconfig all
Friday, February 19, 2010
Lesson 10
Okay, work has been hectic this week so once again I am only getting to this on a Friday! Gotta do it now as I expect to be in Forries before 3!
Quick recap:
802.3 – Ethernet
802.5 – Ring
802.11(x) – Wireless
Key Acronyms:
• FHSS – Frequency Hopping Spread Spectrum
• DSSS - Direct Sequence Spread Spectrum
• Multiplexing – send and receive on same channel
Wireless:
• 802.11
o Has transmission speeds of 1 or 2 Mbps
o Radio frequency of 2.4GHz
o One variation uses FHSS and one uses DSSS
• 802.11.a
o Speeds up to 54Mbps
o 5 GHz band
o Transmission typically at 6, 12 or 24Mbps
o Uses orthogonal frequency division multiplexing (OFDM)
o Range roughly 20 metres
• 802.11b
o Speed – 11Mbps
o 2.4GHz
o Range 100 metres
• 802.11g
o Speed 54Mbps
o 2.5GHz
o Average speeds 20-25Mbps
o Range – 100 metres
• 802.11n
o Speeds up to 300Mbps
o Two streams so 600Mbps
o 2.4GHz or 5GHz frequency
Channels in 802.11b/g Implementation:
Overlap in the radio signals or bleeding can occur when these overlap between adjacent accesses points and clients. The best channels to use to avoid this are channels: 1, 6 and 11.
802.11 Modes:
You get infrastructure and ad hoc modes
Infrastructure mode is when the WAP is hardwired to the network (server) and the workstations connect wirelessly. Uses BSS (basic service set) or ESS (Extended service set) as the protocol
Ad hoc is when the workstations connect to the WAP wirelessly and there is no hardwired backbone. This uses the protocol IBSS (independent basic service set)
WLAN Architecture: see page 190, not important.
Protocols:
• BSS (Basic Service Set)
o One access point connected to a wired network and has one or more wireless stations or clients. A BSS is also referred to as Infrastructure mode as it requires an access point in order to transmit data
• ESS (Extended Service Set)
o The ESS comprises two or more BSS’s that are connected to a common distribution system such as a wired network. An ESS must contain at least two wireless access points operating in infrastructure mode, which allows clients to use their AP depending on the locations of the wireless station or point.
• ESSID (Extended Service Set ID)
o The ESSID is the name that identifies a wireless network or wireless access point so that you can identify the networks clearly.
• IBSS (Independent Basic Service Set
o IBSS does not contain an AP. It is a peer to peer network in which each wireless station or client has its own wireless network adapter and each acts as both client and wireless AP.
802.11 BEACONS
Beacon frames are management frames that are only 50 bytes long. They are used to start and maintain wireless communication. They contain information about the communication process such as the STA and SSID, channel number and security protocol.
Wire Equivalent Privacy (WEP)
• To prevent eavesdropping, IEEE 802.11 WEP defines and algorithm that gives authorised users the same level of security they would on a wired network.
WIFI Protected Access (WPA)
• WPA is a Wi-Fi standard that was designed to improve upon the security flaws of WEP. WPA2 is an upgrade and includes all the 802.11 mandatory standards.
• It improves data encryption through the Temporal Key Integrity Protocol (TKIP).
• WPA adds AES a cipher based CCMP encryption for even greater security.
• User authentication, considered poor over WEP through the EAP (Extensible Authentication Protocol). WEP regulates access to the wireless network based on the computers specific MAC address which is relatively easy to sniff or spoof.
• EAP is built on a more secure public key encryption system to ensure that only the authorised network users can access the network.
Wireless Authentication Methods:
Authentication Method Description
Open System This uses null authentication
Shared Key This authentication method verifies the identity of a station by using a WEP key. Both the station and the AP must be configured to use the data encryption and the same WEP key
802.1x and EAP This authentication method authenticates the user and not the station. A RADIUS server is used – Remote Authentication Dial In Server – the user dials in to the server which disconnects the call and will return the call and reconnect.
Bluetooth
• This is not a network service, it is peer-to-peer
• Bluetooth 1.1 is a wireless protocol used to communicate form device to device in a small area up to 10 metres, transfer is approximately 1Mbps.
• Bluetooth 1.2 increases speed to 2.1-3Mbps and the range increases to about 30 metres.
Networking with TCP/IP
Families and Protocols:
• Successful network communications hinges on them sharing a network protocol to perform various functions related to that communication.
• Network protocols are classified into general families that share common features.
Network Protocols:
Network communications between computers is provided by a network protocol – rules by which network operations are conducted.
There are the following Protocols:
• Network and transport layer protocols
• Application – Presentation- and session layer Protocols
Protocol Bindings:
Assigning a protocol to a network interface card (NIC) is referred to as protocol binding. Multiple protocols can be bound to a single NIC. The NIC can use any of the protocols that are bound to it to communicate with other nodes on the network.
Binding order:
A network interface bound with multiple protocols attempts to connect to a receiving node by testing its available protocols, one by one until it finds a protocol that the receiving node answers.
The TCP/IP Protocol:
This is a protocol suite which works at the network and transport layers of the OSI model. Providing the protocol family functions of reliability, connection and routing.
TCP/IP
The transmission Control/Internet protocol (TCP/IP) is a non-proprietary, routable network protocol suit that enables computers to communicate over all types of networks. TCP/IP is the native protocol of the Internet and is required for Internet connectivity.
IPv4 Addresses:
An IPv4 Address is a 32 bit binary number assigned to a computer on a TCP/IP Network. The 32 bit binary IP Address is usually separated by dots into four 8 bit octets.
• Binary = 11010000.01111011.00101101.00010010
• Decimal = 208.123.45.18
Dotted decimal Notation – this is how TCP/IP address is usually displayed!
An IP address is like a mailing address:
Some of the numbers in the IP address identify the network segment on which computer resides, just as a person mailing address uses a street name etc.
Binary and Decimal Conversion:
Binary is a base 2 numbering system in which any bit in the number is either 1 or 0
Standard Speed Frequency Approximate Range
802.11 1-2Mbps 2.4GHz 100 metres
802.11a 54Mbps 5GHZ 20 metres
802.11b 11Mbps 2.4GHz 100 metres
802.11g 54Mbps 2.4GHz 100 metres
802.11n 300Mbps 2.4 or 5MHz 70 metres
Well that is it for now - see you all tomorrow.
Quick recap:
802.3 – Ethernet
802.5 – Ring
802.11(x) – Wireless
Key Acronyms:
• FHSS – Frequency Hopping Spread Spectrum
• DSSS - Direct Sequence Spread Spectrum
• Multiplexing – send and receive on same channel
Wireless:
• 802.11
o Has transmission speeds of 1 or 2 Mbps
o Radio frequency of 2.4GHz
o One variation uses FHSS and one uses DSSS
• 802.11.a
o Speeds up to 54Mbps
o 5 GHz band
o Transmission typically at 6, 12 or 24Mbps
o Uses orthogonal frequency division multiplexing (OFDM)
o Range roughly 20 metres
• 802.11b
o Speed – 11Mbps
o 2.4GHz
o Range 100 metres
• 802.11g
o Speed 54Mbps
o 2.5GHz
o Average speeds 20-25Mbps
o Range – 100 metres
• 802.11n
o Speeds up to 300Mbps
o Two streams so 600Mbps
o 2.4GHz or 5GHz frequency
Channels in 802.11b/g Implementation:
Overlap in the radio signals or bleeding can occur when these overlap between adjacent accesses points and clients. The best channels to use to avoid this are channels: 1, 6 and 11.
802.11 Modes:
You get infrastructure and ad hoc modes
Infrastructure mode is when the WAP is hardwired to the network (server) and the workstations connect wirelessly. Uses BSS (basic service set) or ESS (Extended service set) as the protocol
Ad hoc is when the workstations connect to the WAP wirelessly and there is no hardwired backbone. This uses the protocol IBSS (independent basic service set)
WLAN Architecture: see page 190, not important.
Protocols:
• BSS (Basic Service Set)
o One access point connected to a wired network and has one or more wireless stations or clients. A BSS is also referred to as Infrastructure mode as it requires an access point in order to transmit data
• ESS (Extended Service Set)
o The ESS comprises two or more BSS’s that are connected to a common distribution system such as a wired network. An ESS must contain at least two wireless access points operating in infrastructure mode, which allows clients to use their AP depending on the locations of the wireless station or point.
• ESSID (Extended Service Set ID)
o The ESSID is the name that identifies a wireless network or wireless access point so that you can identify the networks clearly.
• IBSS (Independent Basic Service Set
o IBSS does not contain an AP. It is a peer to peer network in which each wireless station or client has its own wireless network adapter and each acts as both client and wireless AP.
802.11 BEACONS
Beacon frames are management frames that are only 50 bytes long. They are used to start and maintain wireless communication. They contain information about the communication process such as the STA and SSID, channel number and security protocol.
Wire Equivalent Privacy (WEP)
• To prevent eavesdropping, IEEE 802.11 WEP defines and algorithm that gives authorised users the same level of security they would on a wired network.
WIFI Protected Access (WPA)
• WPA is a Wi-Fi standard that was designed to improve upon the security flaws of WEP. WPA2 is an upgrade and includes all the 802.11 mandatory standards.
• It improves data encryption through the Temporal Key Integrity Protocol (TKIP).
• WPA adds AES a cipher based CCMP encryption for even greater security.
• User authentication, considered poor over WEP through the EAP (Extensible Authentication Protocol). WEP regulates access to the wireless network based on the computers specific MAC address which is relatively easy to sniff or spoof.
• EAP is built on a more secure public key encryption system to ensure that only the authorised network users can access the network.
Wireless Authentication Methods:
Authentication Method Description
Open System This uses null authentication
Shared Key This authentication method verifies the identity of a station by using a WEP key. Both the station and the AP must be configured to use the data encryption and the same WEP key
802.1x and EAP This authentication method authenticates the user and not the station. A RADIUS server is used – Remote Authentication Dial In Server – the user dials in to the server which disconnects the call and will return the call and reconnect.
Bluetooth
• This is not a network service, it is peer-to-peer
• Bluetooth 1.1 is a wireless protocol used to communicate form device to device in a small area up to 10 metres, transfer is approximately 1Mbps.
• Bluetooth 1.2 increases speed to 2.1-3Mbps and the range increases to about 30 metres.
Networking with TCP/IP
Families and Protocols:
• Successful network communications hinges on them sharing a network protocol to perform various functions related to that communication.
• Network protocols are classified into general families that share common features.
Network Protocols:
Network communications between computers is provided by a network protocol – rules by which network operations are conducted.
There are the following Protocols:
• Network and transport layer protocols
• Application – Presentation- and session layer Protocols
Protocol Bindings:
Assigning a protocol to a network interface card (NIC) is referred to as protocol binding. Multiple protocols can be bound to a single NIC. The NIC can use any of the protocols that are bound to it to communicate with other nodes on the network.
Binding order:
A network interface bound with multiple protocols attempts to connect to a receiving node by testing its available protocols, one by one until it finds a protocol that the receiving node answers.
The TCP/IP Protocol:
This is a protocol suite which works at the network and transport layers of the OSI model. Providing the protocol family functions of reliability, connection and routing.
TCP/IP
The transmission Control/Internet protocol (TCP/IP) is a non-proprietary, routable network protocol suit that enables computers to communicate over all types of networks. TCP/IP is the native protocol of the Internet and is required for Internet connectivity.
IPv4 Addresses:
An IPv4 Address is a 32 bit binary number assigned to a computer on a TCP/IP Network. The 32 bit binary IP Address is usually separated by dots into four 8 bit octets.
• Binary = 11010000.01111011.00101101.00010010
• Decimal = 208.123.45.18
Dotted decimal Notation – this is how TCP/IP address is usually displayed!
An IP address is like a mailing address:
Some of the numbers in the IP address identify the network segment on which computer resides, just as a person mailing address uses a street name etc.
Binary and Decimal Conversion:
Binary is a base 2 numbering system in which any bit in the number is either 1 or 0
Standard Speed Frequency Approximate Range
802.11 1-2Mbps 2.4GHz 100 metres
802.11a 54Mbps 5GHZ 20 metres
802.11b 11Mbps 2.4GHz 100 metres
802.11g 54Mbps 2.4GHz 100 metres
802.11n 300Mbps 2.4 or 5MHz 70 metres
Well that is it for now - see you all tomorrow.
Friday, February 12, 2010
Lesson 9
Quick Lesson 8 Re-cap – HOT TIP
Ethernet Frames can have a total size of 1526 bytes – the data at a maximum or 1500 bytes
The minimum can be 72 bytes where the data is at the minimum of 46 bytes
Lesson 9
IEEE Standards
• A family of Networking standards developed by the IEEEE in 1980 to address the rapid changes in networking technology. The 802.x standards are divided into several sub-categories to address the different requirements.
We work with 3 main standards:
1. 802.3 – Ethernet (CSMA/CD)
2. 802.5 – Ring
3. 802.11 - Wireless
802.3 Standard
• IN addition to the media type (cable) 802.3 also defines the transmission speed and signal method.
10 Base standard
• This describes the type of media used and the speeds at which each type of media operates. The cable specification contains three components
• A number indicating the speed
• The signal type in baseband or broadband
• The code for either copper or fiber
The codes and physical media are as follows:
T – UTP or STP (cat3,4,5,5e)
F – Fiber optic
FL – Fiber optic link
FX – Fiber optic using 2 pairs of multimode fiber
10Mbps table below:
10Base-2
Standard Specification Medium Distance
10Base-2 IEEE 802.3a Thinnet Coax 185 metres
10Base-5 IEEE 802.3 ThickNet 500 metres
Fast Ethernet
Standard Specification Medium Distance
100Base-T IEEE 802.3u Cat 5 UTP 100 metres
Gigabit Ethernet (1000 Mbps)
Standard Specification Medium Distance
1000Base-T IEEE 802.3ab Cat 5e or Cat 6 UTP 100 metres
Token Ring Networks
Token-based Media Access
• Media access method in which computers pass a special sequence of bits called a token between them. Only the node holding the token can transmit on the network.
Token Ring Standards – these use a MAU NOT a Hub
• There are two token ring standards that are very similar. IBM Token Ring and IEEE 802.5
Token Ring Characteristics IBM Token Ring IEEE 802.5
Transmission Speed 4/16 Mbps 4/16Mbps
Media Type Star Not Specified
Signalling Baseband Baseband
Access Method Token Passing CSMA/CA Token Passing
Token States
Token State Description
Available There is no data in the payload and the token may be captured for use
Captured There is a valid data payload
Acknowledged Notification of either ACK or NACK positive or negative
Reserved A priority system, in which the token can be reserved
Token ring Access Priority
• Token ring networks use a priority system that permits certain user designated high priority stations to use the network more frequently. They have a priority and reservation field.
MAU (Multi-station Access Unit) – sometimes called a MSAU
• MAU’s can be wired together to form a ring using patch cables and lobe cables for connections.
• A MAU has the same function as a switch.
Token Ring Failure Recovery
• Token ring networks take on a star configuration when a device is turned off or disconnected from the network. IN this situation the MAU simply bypasses the disconnected device, when the device is online but not responsive the MAU will keep the connection live but breaks the ring because the device is not passing data.
Fiber Distributed Data Interface (FDDI) – 802.5 (ring)
Ring 802.5 has an IN and OUT port on the NIC, for FDDI has 2X IN and 2X OUT
This is not very important but nice to know.
It is a networking ring technology that uses double single mode or multimode fiber that operate at 100Mbps.
• Dual Ring
o FDDI ring does not have a device such as a MAU to remove stations when they are turned off. Second fiber transceivers cannot be configured to reverse, there is receive hardware and transmit hardware.
• FDDI Connection Devices
o Nodes are connected to the FDDI in one of two ways.
In dual attached stations (DAS) nodes are connected directly to both the primary and secondary rings
IN single attached stations (SAS) node are connected to a concentrator which is connected to both rings. – Here the concentrator gives the SAS access to the primary ring.
FDDI Failure recovery
• DAS nodes provide fault tolerance measure that detects loss if connectivity and then loop back the signal.
Ethernet Frames can have a total size of 1526 bytes – the data at a maximum or 1500 bytes
The minimum can be 72 bytes where the data is at the minimum of 46 bytes
Lesson 9
IEEE Standards
• A family of Networking standards developed by the IEEEE in 1980 to address the rapid changes in networking technology. The 802.x standards are divided into several sub-categories to address the different requirements.
We work with 3 main standards:
1. 802.3 – Ethernet (CSMA/CD)
2. 802.5 – Ring
3. 802.11 - Wireless
802.3 Standard
• IN addition to the media type (cable) 802.3 also defines the transmission speed and signal method.
10 Base standard
• This describes the type of media used and the speeds at which each type of media operates. The cable specification contains three components
• A number indicating the speed
• The signal type in baseband or broadband
• The code for either copper or fiber
The codes and physical media are as follows:
T – UTP or STP (cat3,4,5,5e)
F – Fiber optic
FL – Fiber optic link
FX – Fiber optic using 2 pairs of multimode fiber
10Mbps table below:
10Base-2
Standard Specification Medium Distance
10Base-2 IEEE 802.3a Thinnet Coax 185 metres
10Base-5 IEEE 802.3 ThickNet 500 metres
Fast Ethernet
Standard Specification Medium Distance
100Base-T IEEE 802.3u Cat 5 UTP 100 metres
Gigabit Ethernet (1000 Mbps)
Standard Specification Medium Distance
1000Base-T IEEE 802.3ab Cat 5e or Cat 6 UTP 100 metres
Token Ring Networks
Token-based Media Access
• Media access method in which computers pass a special sequence of bits called a token between them. Only the node holding the token can transmit on the network.
Token Ring Standards – these use a MAU NOT a Hub
• There are two token ring standards that are very similar. IBM Token Ring and IEEE 802.5
Token Ring Characteristics IBM Token Ring IEEE 802.5
Transmission Speed 4/16 Mbps 4/16Mbps
Media Type Star Not Specified
Signalling Baseband Baseband
Access Method Token Passing CSMA/CA Token Passing
Token States
Token State Description
Available There is no data in the payload and the token may be captured for use
Captured There is a valid data payload
Acknowledged Notification of either ACK or NACK positive or negative
Reserved A priority system, in which the token can be reserved
Token ring Access Priority
• Token ring networks use a priority system that permits certain user designated high priority stations to use the network more frequently. They have a priority and reservation field.
MAU (Multi-station Access Unit) – sometimes called a MSAU
• MAU’s can be wired together to form a ring using patch cables and lobe cables for connections.
• A MAU has the same function as a switch.
Token Ring Failure Recovery
• Token ring networks take on a star configuration when a device is turned off or disconnected from the network. IN this situation the MAU simply bypasses the disconnected device, when the device is online but not responsive the MAU will keep the connection live but breaks the ring because the device is not passing data.
Fiber Distributed Data Interface (FDDI) – 802.5 (ring)
Ring 802.5 has an IN and OUT port on the NIC, for FDDI has 2X IN and 2X OUT
This is not very important but nice to know.
It is a networking ring technology that uses double single mode or multimode fiber that operate at 100Mbps.
• Dual Ring
o FDDI ring does not have a device such as a MAU to remove stations when they are turned off. Second fiber transceivers cannot be configured to reverse, there is receive hardware and transmit hardware.
• FDDI Connection Devices
o Nodes are connected to the FDDI in one of two ways.
In dual attached stations (DAS) nodes are connected directly to both the primary and secondary rings
IN single attached stations (SAS) node are connected to a concentrator which is connected to both rings. – Here the concentrator gives the SAS access to the primary ring.
FDDI Failure recovery
• DAS nodes provide fault tolerance measure that detects loss if connectivity and then loop back the signal.
Subscribe to:
Comments (Atom)